وبلاگ
Ethereum: What is a Finney attack?
Ethereum Finney attack: Understanding its purpose, prerequisites and methods
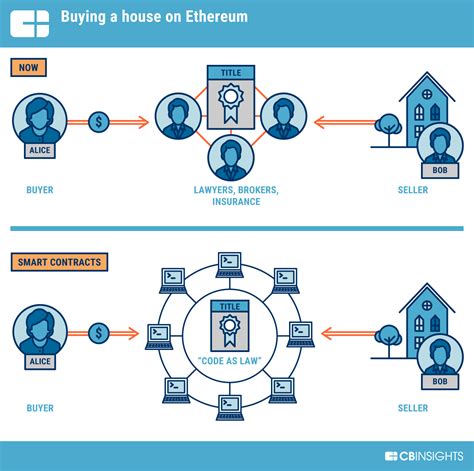
Ethereum, one of the main blockchain platforms, was vulnerable to the type of operation known as the “subtle attack”. This harmful technique allows attackers to manipulate the history of Ethereum network transactions by potentially interrupting the safety and integrity of the network.
What is a fine attack?
Finish attack is a double -price attack that uses the decentralized nature of blockchain transactions. It works by creating false transactions with the same pair of multi-assessments as an existing transaction on the Ethereum network. Therefore, the attacker transmits these false transactions, which are essentially duplicated by the original.
The main purpose of the subtle attack is to manipulate the history of network transactions and to create discrepancies in blockchain. This can lead to various problems, including:
* Loss of trust : If a significant number of users start to refuse new transactions as not valid due to fakes, this can undermine Ethereum network confidence.
* increased price : flooding the network with duplicate transactions, attackers can increase commissions for legal users, leading to higher costs and reducing acceptance.
Prerequisites for Attack on Fine
In order to attack the subtle, the attacker must have two things:
- The ability to create counterfeit transactions : The attacker must be able to generate transactions that correspond to the pair receivers sending a transaction existing on the Ethereum network.
- Access to multiple accounts with sufficient funds : The attacker requires access to at least one balance with a balance enough to support the creation of duplicate transactions.
How does the finner attack work?
Here is a step -by -step explanation of the process:
- Select an attacked user account : Select an Ethereum portfolio that has two or more accounts with sufficient funds.
- Creating counterfeit transactions
: uses tools such as Metamask to create fake transactions that match the pair separated receivers to an existing transaction on the Ethereum network.
- Transmission of fake transactions : transmits these duplicate transactions to the Ethereum network, appearing to be spent.
Origin of the name “Finney Attack”
Finny’s attack is named by Sir Charles KF Finney, a British banker and financier, who was decisive in the development of the first London exchange bag. In 1872, the company of Finney developed millions of dollars transactions every day, making it one of the most skilled traders of his time.
The term “attack of subtle” is probably chosen because it emphasizes the audacity and refinement of the attack that uses the decentralized nature of blockchain technology to manipulate the network.



